by Jeremy Abram – JeremyAbram.net
Introduction: The Hidden Life of Your Digits
Your phone number used to be a simple way to stay connected — a direct line to friends, family, and work. Today, it’s one of the most persistent identifiers in the digital ecosystem. Unlike email addresses, which can be easily changed or compartmentalized, your phone number sticks with you. It’s used for everything from two-factor authentication to customer rewards programs — and that permanence has made it a goldmine for data brokers and automated bots alike.
This article explores how phone numbers are harvested, resold, misused, and ultimately weaponized — and what “phone number hygiene” really means in 2025.
1. The Anatomy of a Digital Identifier
A phone number is no longer just a contact endpoint. It’s a quasi-permanent digital fingerprint. Modern algorithms can link a number to:
- Full names, addresses, and social profiles
- Past and current employers
- Online accounts and purchasing behavior
- Geolocation metadata from app permissions
- Identity graph data (connections to friends, relatives, and coworkers)
Data brokers combine this information into massive “identity bundles” — records that merge phone numbers with browsing history, ad IDs, and social graphs. These datasets are sold to marketers, verification services, and unfortunately, spammers and scammers.
2. How Phone Numbers Get Harvested
Phone number exposure often starts innocently. The following are the most common pathways through which bots and scrapers collect active numbers:
a. Public Social Media Posts
Users post numbers in bios, comments, or business pages. Automated crawlers continuously scrape these platforms, indexing numbers associated with real names and topics.
b. Data Leaks and Breaches
Whenever an app, retailer, or cloud database is breached, exposed tables often contain unencrypted phone fields. Many of these leaks — from ride-share apps to food delivery services — feed directly into spam networks.
c. Caller ID and Reverse Lookup APIs
Services designed for “identity verification” or “spam detection” often operate on pooled datasets. By simply uploading a contact list, the user unknowingly expands the service’s database of known numbers.
d. Messaging Apps and Contact Sync
Apps like WhatsApp, Telegram, and even mainstream platforms encourage you to “sync contacts.” Those contacts are hashed, matched, and compared to global directories — creating a massive relational web that can be monetized or exploited.
e. Lead Forms and Online Registrations
Every contest, job board, or small business landing page asking for a phone number might store or resell it. “Lead enrichment” services thrive on these unregulated submissions.
3. The Lifecycle of a Compromised Number
Once a phone number escapes into circulation, it rarely comes back.
Here’s what typically happens:
- Collection: A bot scrapes or a company leaks your number.
- Validation: The number is pinged through messaging APIs to confirm it’s active.
- Categorization: It’s tagged (e.g., “male, 35–44, automotive interests”).
- Resale: It’s sold in bulk to advertisers or spam networks.
- Recycling: When spam filters or users block it, the dataset is re-filtered, cleaned, and re-sold again under new labels.
The same number may appear in dozens of different lists, each one slightly more enriched than the last.
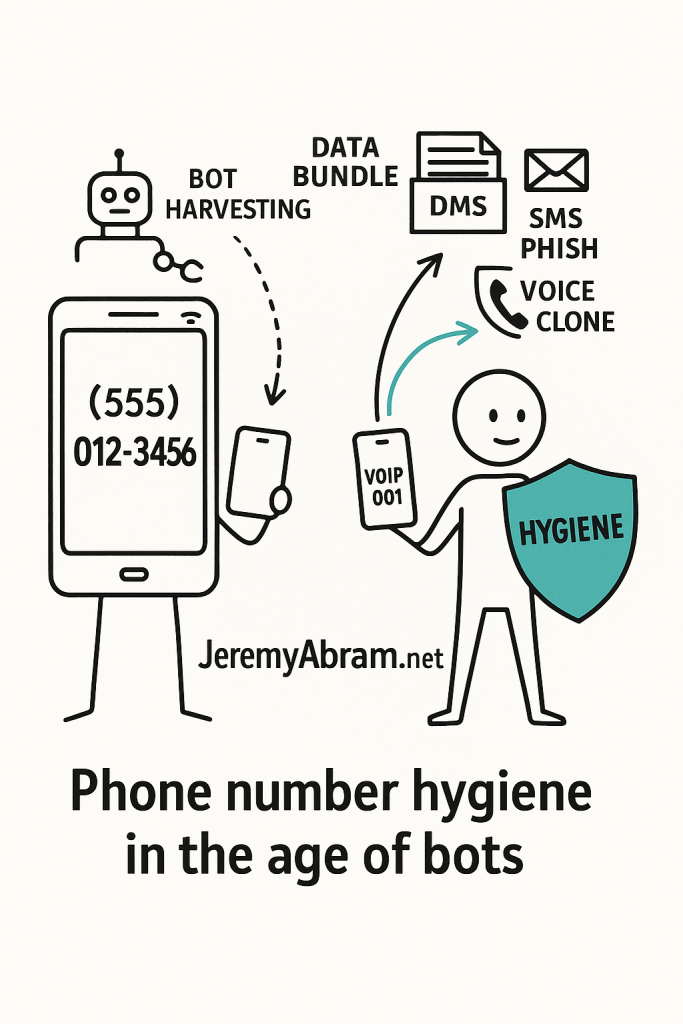
4. The Age of Bots and Automated Exploitation
In 2025, human telemarketers are the minority. Bots handle the bulk of modern spam — using predictive dialing, AI voice synthesis, and SMS flooding to exploit every open channel.
Key trends include:
- AI-Generated Voicemails: Bots craft personalized audio that mimics human sales reps.
- SMS Phishing at Scale: Automated text campaigns mimic delivery notifications or banking alerts.
- Voice Spoofing & Number Cloning: Attackers replicate legitimate caller IDs to bypass spam filters.
- Data Cross-Linking: Bots analyze responses to refine lists and improve engagement accuracy.
These behaviors blur the line between marketing automation and cyber exploitation — both fueled by the same raw ingredient: your phone number.
5. Practicing “Phone Number Hygiene”
Just as you maintain password hygiene, phone number hygiene is about minimizing exposure and controlling reuse.
a. Use Dedicated Numbers for Different Contexts
- One number for personal contacts
- One for business or e-commerce
- One virtual or VoIP number for online registrations and two-factor logins
Services like Google Voice, MySudo, or Privacy.com’s Relay Phone let you mask your real number.
b. Audit Where Your Number Lives
Search your own number (in quotes) online — you might be surprised how many data broker sites list it. Many allow opt-out requests.
c. Avoid “Free Lookup” Temptations
Reverse lookup sites often double as data harvesters. Searching someone’s number adds your query to their analytics.
d. Resist Contact Sync
Unless absolutely necessary, deny contact-sync permissions in messaging and social apps.
e. Rotate, Expire, or Alias
For high-risk or public-facing work, consider disposable VoIP numbers that can expire or be rerouted.
6. The Bigger Picture: Privacy as a Lifecycle
Phone number exposure is part of a larger data hygiene ecosystem. Every identifier — email, IP, ad ID, biometric — becomes a thread in a profile tapestry. Unlike cookies, phone numbers can’t be deleted or easily replaced.
That makes them uniquely dangerous in the age of persistent bots, where automation can exploit even the smallest exposure instantly and endlessly. True privacy, then, isn’t about hiding — it’s about limiting linkage.
Conclusion: The Price of Permanence
Our digital infrastructure still treats the phone number like a safe, human identifier — when in reality, it has become a universal key. Each time we use it, we unlock a door that can’t be closed again.
Practicing phone number hygiene is not paranoia; it’s pragmatism. It means recognizing that behind every missed call and every random text, there’s likely an algorithm connecting dots — and your digits might be one of them.
Recommended Further Reading on JeremyAbram.net
- “The Invisible Data Trail” – How minor metadata builds full digital profiles
- “Ghost Permissions” – Hidden data sharing inside your favorite apps
- “The Mic That Never Sleeps” – How passive listening reshapes digital trust
Leave a Reply