A step‑by‑step hardening guide for apps, data, and daily use
Written for JeremyAbram.net
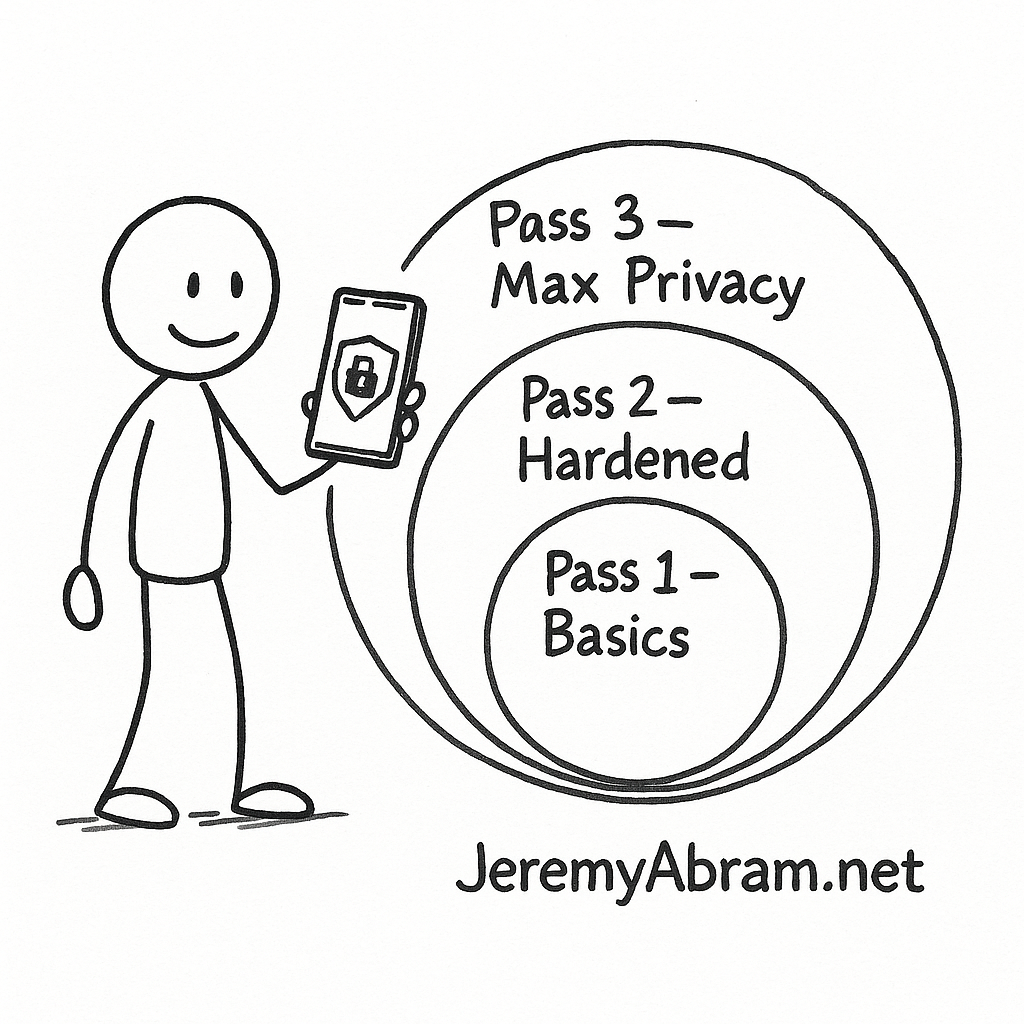
This guide is organized in three passes—Basics (15–30 min), Hardened (45–90 min), and Max Privacy (advanced)—so you can stop at any level and still end up safer than 99% of users. Each step explains what to do and why it matters.
Read this first: What “privacy” means on Android
- Data minimization: Share the least possible data (identifiers, location, contacts, media).
- Surface reduction: Fewer apps/services with broad privileges → smaller attack and tracking surface.
- Local-first: Keep data on-device when feasible (notes, passwords, maps caches).
- Network hygiene: Encrypt DNS, block trackers, and sandbox apps.
- Behavioral hygiene: Lock screen discipline, cautious linking, least-privilege mindset.
Reality check: You can reach excellent privacy without breaking daily usability. The trick is using built-in controls well, and replacing a few high‑leak apps with privacy‑respecting equivalents when it makes sense.
QUICK CHECKLIST (printable)
Device & Account
- Strong 6+ digit PIN (no pattern); biometrics optional; auto-lock ≤ 30 sec
- Google account: 2FA on; recovery info updated; passkeys enabled
- Web & App Activity: Paused; Location History: Off; Ad Personalization: Off; Delete Advertising ID
System Settings
- Private DNS: enabled (e.g.,
dns.quad9.net,dns.adguard.com) - Wi‑Fi/Bluetooth scanning: Off; MAC randomization: On; Nearby Share: Contacts only or Off
- Location: “Only while in use”; precise on only when needed
- Permissions: Auto‑reset for unused apps On; Photo Picker (selective access) used by default
- Notifications on lock screen: “Sensitive content hidden”
- Developer options: USB debugging Off; OEM unlock Off; “Sensors Off” tile added
Apps & Stores
- Uninstall bloat; restrict Play Services; disable preinstalled trackers where possible
- Prefer privacy‑respecting stores (F‑Droid); use Aurora Store for Play without linking account
- Browser: Firefox (uBlock Origin), Brave, or Vanadium (GrapheneOS)
- Keyboard: AnysoftKeyboard/FlorisBoard (offline) or Gboard with network dictation off
- Maps: Organic Maps/OsmAnd for local tasks; use Google Maps only when needed
- Messaging: Signal as default for secure chats; RCS/SMS only when required
Network & Blocking
- Tracker/DNS firewall: RethinkDNS, AdGuard, or Nebulo; VPN only from reputable providers
- Per‑app network controls: block background data for apps that don’t need it
Data Hygiene
- EXIF removal on shares; clipboard auto‑clear; safety check for permissions quarterly
- Backups: encrypted local or end‑to‑end cloud (e.g., Signal, Photos alternatives)
PASS 1 — BASICS (15–30 minutes)
1) Lock screen & encryption
Do: Set a 6+ digit PIN (Settings → Security & privacy → Screen lock). Turn Auto‑lock to 30s–1min. Optionally enable fingerprint/face for convenience, but keep PIN as primary. Ensure Lockdown is accessible from power menu (temporarily disables biometrics).
Why: Full‑disk encryption hinges on your lock method. Patterns are easily shoulder‑surfed; short PINs are brute‑forceable. Lockdown prevents forced unlocks with biometrics.
2) Google account hygiene
Do:
- Turn on 2‑Step Verification and passkeys. Update recovery email/phone.
- In Google Account → Data & privacy: Pause Web & App Activity, turn off Location History, turn off ad personalization, and Delete / Reset Advertising ID (Android 12+ allows removal).
- In Security Checkup, revoke old devices/app access.
Why: Your Google account is a central data broker. Reducing server‑side logging dramatically shrinks your profile and ad inferences.
3) Network privacy: Private DNS
Do: Settings → Network & Internet → Private DNS → Private DNS provider hostname. Use dns.quad9.net (malware blocking) or dns.adguard.com (ad/track blocking).
Why: Encrypts DNS lookups (DoT), blocking passive observers and enabling network‑level filtering without a VPN.
4) Location sanity
Do:
- Settings → Location → App permissions: set “Allow only while in use.” Disable precise for apps that only need city‑level location.
- Turn Wi‑Fi & Bluetooth scanning off (Location → Scanning) unless you truly rely on it.
- Disable Nearby Share or set to Contacts only.
Why: Many apps request location by default. Precise + background access is highly identifying.
5) Permissions discipline (the 3 rules)
Do:
- Deny by default. Approve only when the feature is in active use.
- Prefer Photo Picker (select specific images) over broad media storage permissions.
- Enable Auto‑remove permissions for unused apps (Privacy → Permission manager → Auto‑reset).
Why: Least‑privilege keeps apps sandboxed and limits lateral data access (contacts, calendar, call logs, sensors).
6) Reduce bloat & trackers
Do: Uninstall/disable preinstalled apps you don’t use. For apps you must keep, disable unnecessary permissions/notifications and restrict background data.
Why: Fewer apps → fewer trackers, fewer updates, fewer accidental leaks.
7) Safer defaults for common categories
- Browser: Firefox with uBlock Origin; Brave (built‑in shields); DuckDuckGo for simplicity. Set open links in default browser, disable in‑app browsers when possible.
- Search: DuckDuckGo, Startpage, Brave Search.
- Keyboard: AnysoftKeyboard or FlorisBoard (offline). If using Gboard, disable personalization and networked dictation.
- Maps: Organic Maps / OsmAnd for local/offline; launch Google Maps only when needed.
- Messaging: Signal for E2EE chats + disappearing messages; use RCS/SMS only when necessary.
- Email: Proton, Tutanota, Fastmail (custom domains, robust privacy). On Gmail, disable smart features/data sharing.
- Photos: Simple Gallery or local galleries; when sharing, strip EXIF (many gallery apps add this toggle).
PASS 2 — HARDENED (45–90 minutes)
8) Per‑app network and tracker blocking
Option A: DNS‑only firewall
- Install RethinkDNS or AdGuard (non‑root). Enable DNS‑over‑HTTPS/TLS, choose a blocklist (e.g., OISD/AdGuard), and enable per‑app network rules.
Option B: System‑wide VPN from a reputable provider
- If you need a VPN (public Wi‑Fi, censorship bypass), use a well‑audited provider. Avoid “free” VPNs. Configure always‑on + block connections without VPN when appropriate.
Why: Blocks known trackers and lets you shut off network access for noisy apps. DNS blocking is lightweight and effective for most users.
9) App store strategy (de‑identify where possible)
- F‑Droid: Open‑source, tracker‑light apps (note: slower updates on some repos).
- Aurora Store: Access Google Play anonymously (disposable session) to reduce linkage to your identity.
- Play Store hygiene: If you must use Play, limit purchase and profile info; review Play Protect settings and permissions for Google Play Services.
Why: Store linkage can deanonymize devices; alternative clients reduce this risk for free apps.
10) Work profiles & containment
- Use Shelter or Insular to create a work profile: install higher‑risk apps (e.g., social media) there. Pause the work profile on demand to freeze them.
Why: Profiles sandbox app data and isolate notifications/permissions, giving you a “quarantine” for necessary but invasive apps.
11) Sensors & developer options
- Add the “Sensors Off” tile (Developer options) to quickly disable camera/mic/sensors.
- Keep USB debugging Off; OEM unlocking Off. Only enable when required, then disable again.
Why: Reduces physical compromise risk and lets you cut off sensors when privacy is critical.
12) Tighten lock‑screen & notifications
- Notifications → Sensitive content hidden on lock screen.
- Disable content previews for messaging/email.
- For smart assistants, limit on‑device recognition and disable lock‑screen query access.
Why: Shoulder‑surfing and casual access leaks more data than you think.
13) Data lifecycle & backups
- Prefer end‑to‑end encrypted messengers and backup options (Signal’s encrypted backups; Proton Drive/MEGA E2EE; local encrypted copies).
- Periodically export critical data to local, encrypted storage (SD card/PC) and verify restores.
Why: Privacy without resilience is a trap; you need recoverability without third‑party mining your data.
PASS 3 — MAX PRIVACY (Advanced)
14) Privacy‑centric OS choices
- GrapheneOS (Pixel only): Hardened kernel/userspace, per‑app network/permissions, sandboxed Google Play (optional), robust exploit mitigations.
- CalyxOS (Pixel/selected): Usability‑focused privacy with microG option.
Why: Stock Android can be excellent with tuning, but privacy OSes add meaningful hardening and Google de‑coupling. Caveat: Banking, transit, and DRM apps may require extra steps or may not work.
15) Compartmentalization models
- Persona split: Separate accounts/profiles for Work, Social, Banking, Travel. Distinct apps per profile.
- Device split: A secondary device for high‑risk travel or events (e.g., protests/conferences).
Why: It’s much harder to correlate activity across clean compartments.
16) Network hardening beyond DNS
- Self‑hosted or trusted WireGuard server.
- Firewall first, VPN second: Use DNS firewall for baseline filtering; layer VPN only when you need location masking or hostile‑network protection.
Why: Minimizes trust while keeping performance and battery decent.
17) Supply‑chain and app vetting
- Run new apps through Exodus Privacy reports (tracker & permission audit) and review maintainer reputation.
- Prefer clients that support local accounts and open protocols (e.g., IMAP, Matrix, ActivityPub).
Why: Vetting keeps you out of high‑risk ecosystems.
18) Travel mode & border considerations
- Before travel, create a minimal profile/device with only essential apps and a fresh account; disable biometrics and rely on strong PIN only.
- Use Lockdown at borders; consider airplane mode + sensors off.
Why: Reduces exposure to device searches and coerced unlocks.
Per‑App Permission Playbook (use as a template)
Calendars & Email
- Calendar: Only calendar permission. No location/contacts unless required. No background network if read‑only.
- Email: No contacts (use manual addresses). Disable tracking pixels (client setting).
Cameras & Galleries
- Camera: Permit only when in use. Deny location tagging. Disable cloud auto‑backup if using private galleries.
- Gallery: Use Photo Picker for selective shares. Strip EXIF on share.
Maps & Rideshare
- Location: While in use; precise only when navigating. Turn off background.
- Microphone: Off unless using voice search.
Social Media
- Notifications: Mentions only or Off. Deny contacts, calendar, call logs. Restrict background data. Place in work profile.
Banking/Payments
- Allow only required permissions; keep Play Services updated if app depends on it. No screen overlays or accessibility services alongside banking apps.
Utilities (QR, flashlight, file managers)
- Deny contacts/location/network if not essential. Prefer open‑source utilities from F‑Droid.
Ongoing Maintenance (quarterly checklist)
- Permission audit (Settings → Privacy → Permission manager) and remove stale apps.
- Review Google Account privacy dashboard again.
- Rotate your PIN if exposed and prune saved Wi‑Fi networks you no longer use.
- Check your DNS/firewall logs for noisy apps; tighten rules.
- Verify encrypted backups can restore.
Frequently Asked Trade‑offs
- Do I need a VPN 24/7? No. Use DNS firewall as default; add VPN on hostile or public networks, geo‑restricted tasks, or when your ISP is nosy.
- Are biometrics “bad”? They’re convenient but can be compelled in some jurisdictions. Keep a strong PIN and use Lockdown when needed.
- Will blocking trackers break apps? Sometimes. Add exceptions per app; keep social media in a work profile to contain fallout.
- Can I keep Google Photos/Drive? Yes, but assume server‑side scanning/analysis. Consider local/E2EE alternatives for sensitive material.
Appendix: Suggested Apps & Services (2025)
- Blockers/Firewall: RethinkDNS, AdGuard, NetGuard (no root)
- Stores: F‑Droid (main + Izzy), Aurora Store (anonymous Play)
- Browsers: Firefox + uBlock Origin; Brave; Vanadium (GrapheneOS)
- Maps: Organic Maps, OsmAnd
- Messaging: Signal
- Email: Proton, Tutanota, Fastmail
- Notes: Standard Notes, Joplin (E2EE), Simple Notes (local)
- Cloud E2EE: Proton Drive, Tresorit, MEGA (client‑side), Syncthing (peer‑to‑peer)
- Utilities: Simple Mobile Tools suite, OpenBoard/AnysoftKeyboard, Aegis (2FA), Open Camera
- Audit: Exodus Privacy
© Jeremy Abram — JeremyAbram.net. This guide may be excerpted with attribution and a link back to the canonical source on JeremyAbram.net.
Leave a Reply