Introduction
In today’s digital world, online privacy and data security are more critical than ever. Every time we connect to the internet—whether at home, work, or a public Wi-Fi hotspot—our data travels through various servers and networks, potentially exposing sensitive information. A Virtual Private Network (VPN) is one of the most effective tools for securing online communications, protecting privacy, and enabling unrestricted access to global content.
What is a VPN?
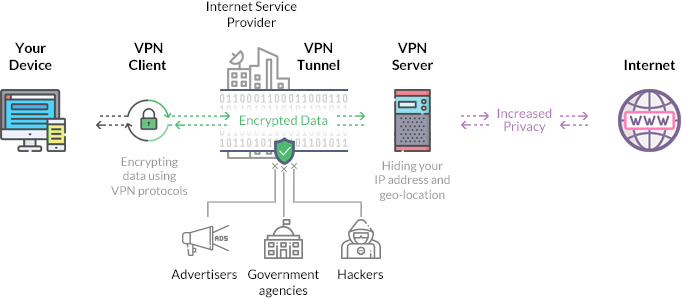
A VPN (Virtual Private Network) is a technology that creates a secure, encrypted tunnel between your device and a remote server operated by the VPN provider. This tunnel hides your IP address and encrypts your internet traffic, making it appear as though you’re browsing from the VPN server’s location instead of your actual one.
In essence, a VPN:
- Masks your IP address, providing anonymity.
- Encrypts data transmission, preventing interception.
- Bypasses geographic restrictions, granting access to blocked or censored content.
How VPNs Work
When you activate a VPN:
- Your device connects to a VPN server through an encrypted connection.
- The VPN client encrypts all the data before it leaves your device.
- The encrypted data is sent to the VPN server, which decrypts it and forwards it to the intended website or online service.
- The response from the website follows the same path in reverse—encrypted by the VPN server and decrypted by your device.
Example
Without a VPN, your data flows directly through your Internet Service Provider (ISP), which can log and monitor your activities. With a VPN, your ISP only sees encrypted traffic to a VPN server—it can’t tell what websites you visit or what data you transmit.
Types of VPNs
1. Remote Access VPN
Used by individuals to connect securely to a private network over the internet. Common in remote work environments.
2. Site-to-Site VPN
Links two or more networks—often used by organizations to securely connect branch offices to a central corporate network.
3. Client-Based VPN
Requires users to install VPN software on their devices to initiate the connection manually.
4. SSL VPN
Uses the Secure Sockets Layer (SSL) protocol, allowing secure connections through a web browser without installing additional software.
VPN Protocols
VPNs use various protocols that define how data is transmitted and secured. The most common include:
| Protocol | Description | Security Level | Speed |
|---|---|---|---|
| OpenVPN | Open-source, highly secure, supports multiple encryption methods | High | Moderate |
| IKEv2/IPSec | Stable and fast, especially for mobile users switching networks | High | Fast |
| WireGuard | Modern, lightweight, open-source protocol known for performance | Very High | Very Fast |
| L2TP/IPSec | Layer 2 Tunneling Protocol with IPSec encryption | Moderate | Slow |
| PPTP | Older protocol, less secure | Low | Fast |
Benefits of Using a VPN
🔒 1. Enhanced Privacy and Security
VPNs encrypt your data, protecting it from hackers, ISPs, and even government surveillance. This is especially vital when using public Wi-Fi networks, which are often insecure.
🌍 2. Access to Restricted Content
VPNs let users bypass geo-blocks, allowing access to streaming services, websites, and content unavailable in certain countries.
🕵️♂️ 3. Anonymity Online
By hiding your real IP address, VPNs make it harder for websites and advertisers to track your location and browsing behavior.
🧳 4. Remote Work Support
Businesses rely on VPNs to give employees secure access to company servers and data from remote locations.
💰 5. Potential Cost Savings
Some users use VPNs to find better prices on online purchases (like flights or software) that vary by region.
Limitations and Considerations
Despite their benefits, VPNs are not flawless:
- Speed Reduction: Encryption can slightly slow down connection speeds.
- Trust in VPN Provider: VPN companies can potentially log user data. Always choose one with a no-logs policy and transparent privacy practices.
- Legal Restrictions: Some countries (e.g., China, Russia, UAE) heavily regulate or ban VPN use.
- Compatibility Issues: Some websites and streaming platforms actively block VPN traffic.
Choosing the Right VPN
When selecting a VPN, consider the following factors:
- Strong encryption (AES-256 is standard)
- No-logs policy
- Server network size and locations
- Performance and speed
- Ease of use and cross-platform support
- Customer support and transparency
Top-rated providers (as of 2025) often include NordVPN, ExpressVPN, ProtonVPN, and Surfshark, known for strong privacy protections and fast speeds.
VPNs and Cybersecurity
VPNs are just one layer of defense in a comprehensive cybersecurity strategy. To maximize protection:
- Keep your operating system and applications updated.
- Use antivirus software.
- Enable two-factor authentication (2FA).
- Avoid sharing personal data on insecure websites.
The Future of VPN Technology
Emerging trends indicate that VPNs are evolving toward:
- Integration with AI for threat detection and adaptive routing.
- Quantum-resistant encryption to safeguard against future cryptographic threats.
- Privacy mesh networks offering decentralized VPN infrastructures for enhanced trust and resilience.
Conclusion
A Virtual Private Network (VPN) is an essential tool in today’s digital landscape, safeguarding privacy, enhancing security, and enabling open access to global content. Whether for personal browsing, remote work, or cybersecurity, understanding how VPNs function empowers users to make informed choices about their online protection.
Leave a Reply